Featured
Table of Contents
Vpn Vs Tor Vs Proxy Servers In 2023: Stay Anonymous ...
Unlike Tor, which just secures demands while using the web browser, VPNs are able to encrypt all the traffic coming from your computer system. This makes them more safe. For a VPN to work, it requires to run effectively. VPN leaks prevail if the software isn't set up and checked effectively. While some VPNs have complimentary choices, the more safe and secure variations cost cash.
While both Tor and VPNs work to safeguard your online anonymity, VPNs are the most protected option if used effectively.
VPNs are fast, secure all your traffic, give you access to any Web site and put you in control of your meant location. When looking for the best VPN, make sure you install it effectively and know how the business safeguards your data. For example, the Panda VPN does not keep logs and walks you through proper setup.
When To Use Tor Or A Vpn - Privadovpn
Tor or VPN? The fact is, it's not an apples to apples contrast, and given that you actually appreciate your personal privacy and security, I'm going to give you a fundamental understanding of how each of these tools work and the specific jobs they're developed for. Be sure to sign up for the All Things Safe You, Tube channel!.?.!! There's one important question you require to ask when deciding whether to use Tor or VPN.
Which's why a nuanced response is essential when comparing Tor vs VPN.Now I'm going to provide an overview comparison in between Tor and VPN, and after that use one more lesser-known service that integrates the strengths of both of these tools into one. A few of the links in this article may be affiliate links, which implies that at no extra cost to you, I might be compensated if you pick to use one of the services listed.
I cover it up in another envelope addressed to a various pal and do not put my return address on it.: When I offer this envelope to the mailman, he doesn't know where the letter will ultimately wind up, he feels in one's bones to provide it to my buddy. When my buddy gets the envelope, he does not know where it originated from considering that it has no return address, all he understands is that when he opens it up, there are directions to offer it to my moms and dads.
Tor Vs. Vpn - Which Online Privacy System Is Better? 2023
Spoiler alert: unless I sign my name to it. That is Tor. This method supplies a great deal of privacy, and is the finest alternative for those who are genuinely concerned about somebody following their internet traffic. But Tor does have weaknesses. Let's take an appearance at a few of them.: Utilizing Tor is sluggish, which makes sense if you consider all that's occurring with the data when it travels through the Tor network.
Due To The Fact That The Tor Project publishes the full list of exit nodes, there are a lot of online services that either block access to their website for anyone that comes from among these exit nodes, or they force repetitive security difficulties such as CAPTCHA and others measures. This implies that when utilizing Tor, instead of having freer access to the web, you may discover yourself a bit more restricted.
This means that any other app or data transfer on your gadget that does not go through this browser does not receive the personal privacy benefits of the Tor network. A system-wide or device-wide Tor connection is possible, but it's not going to be easy to establish for the typical individual.
The Difference Between Tor And Vpn's Explained
Over the years, numerous security consultants and scientists have actually claimed methods to compromise the integrity of the Tor network. Mind you, unless your communications are high worth, it's unlikely any person would make the effort to do this. The most likely situation is that, nearly as if I had actually signed the letter to my parents.
Oh, and I forgot one last thing. Tor is totally free (which is definitely a benefit). This reliance on volunteers is specifically why the network hasn't grown very quickly over the previous years and it brings up genuine issues about who owns these nodes and why they're ready to absorb the cost of running them for free.
I suggest, there is an extra layer of encryption that happens between you and the VPN server you link to, however once your internet traffic leaves that VPN server, the file encryption is likewise gone, so take that for what it deserves. This is why it bothers me that so much of the VPN industry and much of the influencers and content developers who make cash here, tend to promote privacy and security as the main selling points of a VPN.As I have actually made clear in another article about why you ought to stop using a VPN, the reality is that a virtual personal network is best utilized to avert censorship, secure your IP address and or gain access to georestricted material like Disney+, BBC i, Gamer and more.
Vpns, Tor, I2p — How Does Nym Compare?
And there's always a danger it could be broken. I'm comparing the two side by side here, however as I stated at the very start, this actually isn't an apples to apples comparison. We're comparing a decentralized personal privacy tool, Tor, with a central protected gain access to tool, or VPN.If your information provides a risk to you, Tor is probably your best option.

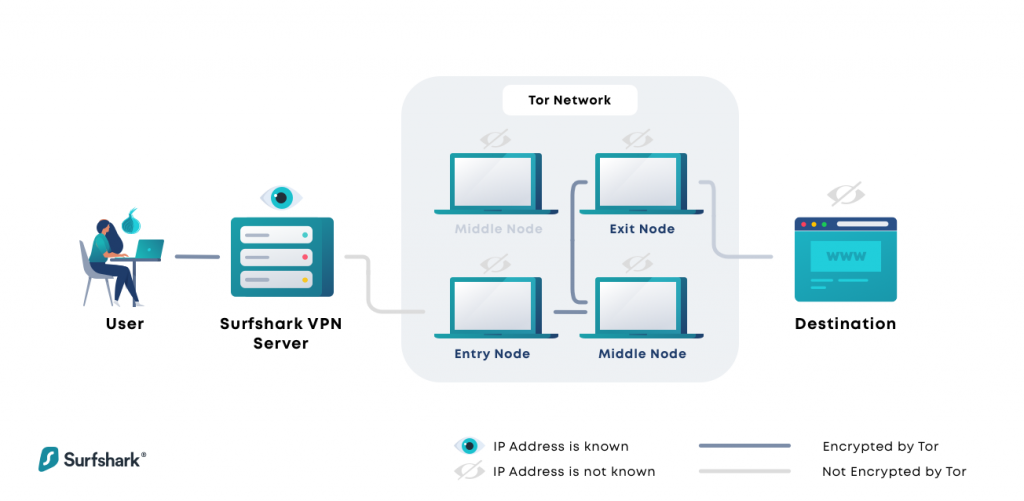
Let's take a fast appearance at some alternatives to Tor and VPN. There's what's understood as Tor over VPN, likewise called "Onion over VPN", where you're essentially linking to a VPN first and then accessing the Tor network from there.
I utilize a service like Mysterium Network as my favored d, VPN and while it's still an innovation in its infancy, it has carried out well for me. I'm not here to declare a winner in between Tor vs VPN or to inform you that you need to utilize one over the other.
Latest Posts
Best Enterprise Infrastructure Vpn Solutions For 2023
Best Vpns For Business In 2023
Best Vpn Locations For Warzone Bot Lobbies 2023