Featured
Table of Contents
Why Wireguard? - Guides
While No Trust is a much more comprehensive subject, one of its useful applications, Zero Trust Network Access (ZTNA), needs a secure interactions channel. This is where Wire, Guard comes in, as it can be. The entire facilities in this usage case depends on endpoints equipped with software application that could use Wire, Guard.
This creates a much better-controlled environment in which the gadget, user identity, and exchange channels are utilized to accomplish the Absolutely no Trust design. While this is a far more complex technique to set up and administer, it's one of the most popular and safe and secure methods to make safe remote access possible.
The landscape of the Internet is an ever-changing environment, and one of the existing collective focal points of it are Virtual Private Networks or VPNs. One can't help however see the uptick in the number of ads of VPN vendors. An appropriate metric of this is the worldwide increase in the search of the term "VPN" in Google through Google Trends.
Wireguard: The Next Generation Vpn Protocol
1: Google Trend Result for Keyword "VPN" In Fig. 1, we can observe an upward trend in the chart for the search term "VPN" with respect to time given that 2014. People worldwide have actually ended up being progressively aware about privacy and handling of their personal information on the Web. There are lots of individual factors that a users would pick to use a VPN such as to bypass censorship firewall softwares in some nations.
It is developed in a compact and protected way and has actually currently been incorporated to the Linux Kernel. The inception of this protocol was borne out of a covert traffic tunneling option that its developer was trying to implement. During his efforts, he realized that procedures like IPsec and Open, VPN ran on large and large codebases, which were harder to debug, handle, and established appropriately.
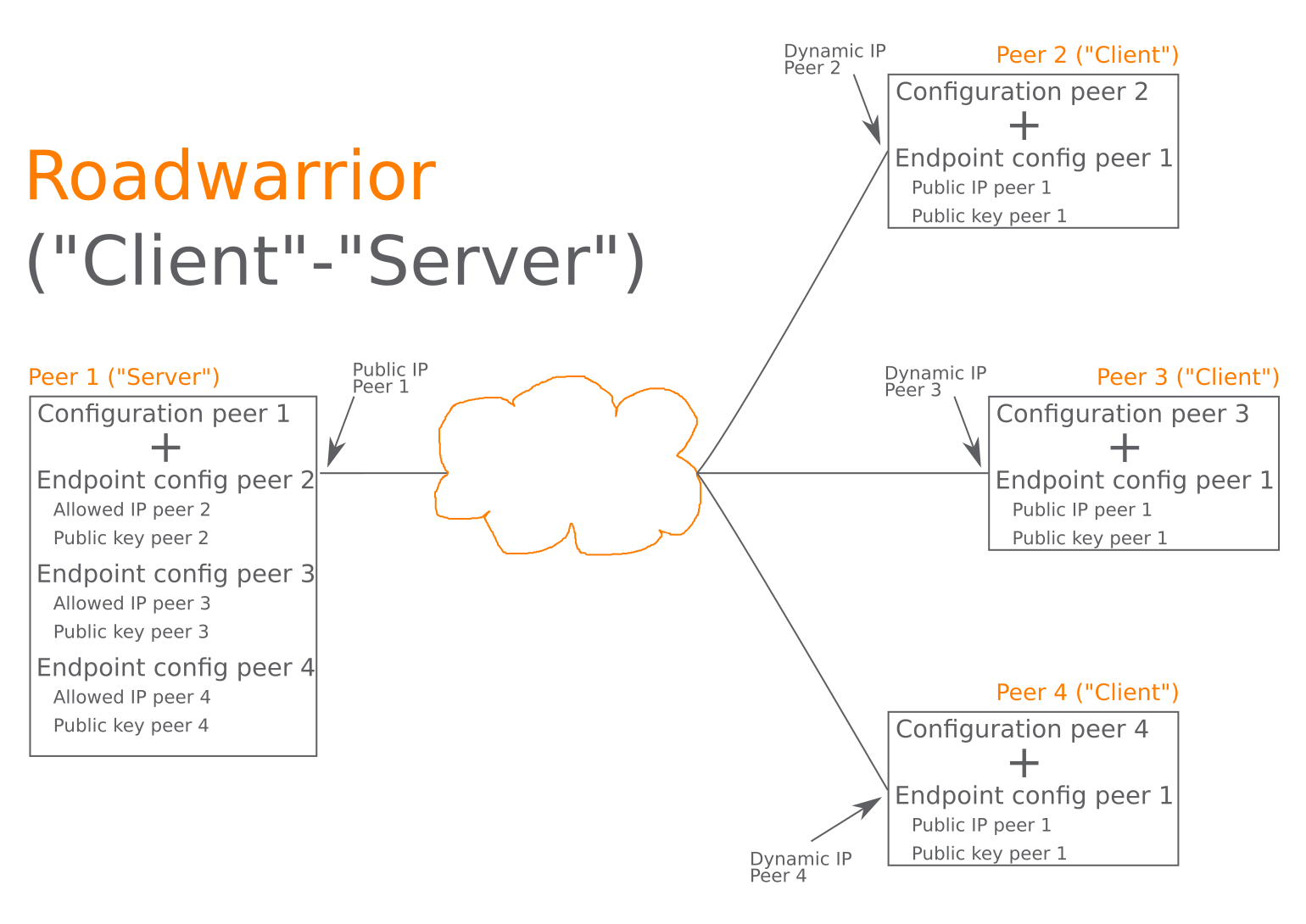
We will now look at some of the interesting functions of the Wire, Guard Procedure in depth. For authentication amongst peers, Wire, Guard utilizes a concept it describes as "Crypto, Key Routing". In this procedure a public and private keypair is created and associated to each peer's IP address.
Ipsec Vs. Wireguard
This interface likewise holds the details of the peers which are allowed to interact with it in the kind of the peer's public secret and tunnel IP. The static public key and tunnel IP info can be distributed amongst the peers through any safe and secure out-of-band approach. Like how circulation of SSH secrets work.
Fig. 2: Wire, Guard Setup file in the VPN Customer Fig. 3: Wire, Guard Configuration file in the VPN Server Wire, Guard appears stateless to the user. Completion user only requires to the configure it as soon as, and that suffices for it to begin and keep working. It is naturally stateful though, and the state management is taken care of by a set of internal timers.
- If there is no action of that handshake for 5 seconds, another handshake is initiated. - If after a recognized connection, no confirmed packages have actually gotten here for 15 seconds, a handshake is started. This is all done immediately, and the user does not have to keep track of it.
What's Wireguard (Vpn/protocol)? Is It Better Than ...
B. Handshake Reaction After the initiation, a reaction is sent out from the responder to the initiator which again holds an unencrypted ephemeral public crucial produced by the responder. It also includes an empty buffer, which has actually been encrypted utilizing a key that is determined based on the ephemeral private key and the fixed key of the initiator.
6: Handshake Action Packet in Wireshark C. Transportation Data Package After the handshake packets are exchanged, shared session secrets are computed based on the exchanged data. There are 2 session keys, one for securing data that will be sent and another for decrypting data that has actually been gotten.

Fig. 7: Transportation Data Package in Wireshark Wire, Guard works over UDP which is an unreliable protocol where messages can sometimes appear out-of-order. To take care of that, Wire, Guard uses a counter field in the information packets combined with an internal moving window to keep track of the packages that have been gotten.
[Wireless Router] How To Set Up Wireguard® Client In Vpn ...
D. Cookie Reply Package As discussed earlier, Wire, Guard utilizes MAC fields in the handshake packages for security factors. If the responder is ever under load from the CPU intense calculations that are occurring in after the Handshake Initiation packet, it may pick to not go ahead with sending out a Handshake Reaction package, but rather can react with a Cookie Reply packet.
Because its debut in 2017, Wire, Guard has garnered beneficial viewpoints from security researchers and well-known tech characters. what is wireguard protocol and how does it work?. This is largely due to the fact that it is much faster than its counterparts, while not compromising with security. It has actually been integrated into the Linux 5. 6 Kernel in March 2020.
The kind of VPN protocol that you use can impact the speed, stability, ease of use, security, and privacy of your connection. Wire, Guard is the latest gamer in the VPN protocol world and has many advantages over older types of protocols. Lots of professionals are delighted about Wire, Guard due to the fact that it cuts the fat to be quicker and lighter than procedures like Open, VPN.
Wireguard Vpn Protocol Is Fast. But Is It Good For Your ...
The most common complaint about Open, VPN is that it's slow. It's not unusual for a video streaming through Open, VPN to become a slideshow. Some users likewise complain about connections dropping on Open, VPN. This is where Wire, Guard is available in. The procedure is steady, faster, less complicated, and simpler to configure than Open, VPN.
Here are the highlights: Wire, Guard was quickest in nearly 60% of the download tests. Wire, Guard is nearly 15% faster than Open, VPN on UDP.Wire, Guard is 56% faster than Open, VPN on TCP. Wire, Guard isn't just fast, it's also very protected. At Malwarebytes, we pair Wire, Guard with a 256-bit AES encryption to secure connections.
Using the very same address each time provides users a predictable ID that's shown every service they utilize, including any marketers seeing on. To counter this, some VPN company customize the VPN procedure so that it designates a random IP address, that makes it harder for marketers, websites, and others to track your activity from one session to the next.
What Is Wireguard? Wireguard Explained
To have a secure, user friendly, and easy VPN solution, Wire, Guard shines as the finest option. Wire, Guard is ideal for both smartphones and totally packed foundation routers.
Wire, Guard was released for the Linux kernel, the primary part of the Linux operating system understood for security and speed. Wire, Guard is a VPN protocol that is popular as a quickly, modern, and protected method to link to a VPN server. It is capable to work on your device utilizing sophisticated cryptography.
Latest Posts
Best Enterprise Infrastructure Vpn Solutions For 2023
Best Vpns For Business In 2023
Best Vpn Locations For Warzone Bot Lobbies 2023